Tailscale
Tailscale
Preface
This article is an introduction and simple configuration of Tailscale.
My configs:
- Controlled device: Linux-Zorin16.3 same as Ubuntu22.04.
- Main device: MacOS14.1
- Tailscale link: https://tailscale.com/
1. Tailscale
1.1 What is Tailscale?
Tailscale is a VPN service that enables encrypted point-to-point connections using the open source WireGuard protocol. It makes the devices and applications you own accessible anywhere in the world, securely and effortlessly Tailscale is a zero-config VPN, where an agent is installed on every device you want on a VPN mesh. This agent sets up a new network endpoint/card on that device and assigns a Tailscale managed IP unique to your login which is static to each device running the agent.
Simply put, tailscale combines all of your computers into a single LAN.
1.2 How to install Tailscale?
The only thing you need is to create an account and install Tailscale on both of your computers.
You can follow this page to do it.
Install: https://tailscale.com/download
Helper: https://tailscale.com/kb/1017/install#need-some-inspiration
Tips:
For Mac, I am sorry to say that Tailscale can’t be found in China’s AppStore.
After adding your device, you can find its address on this page.
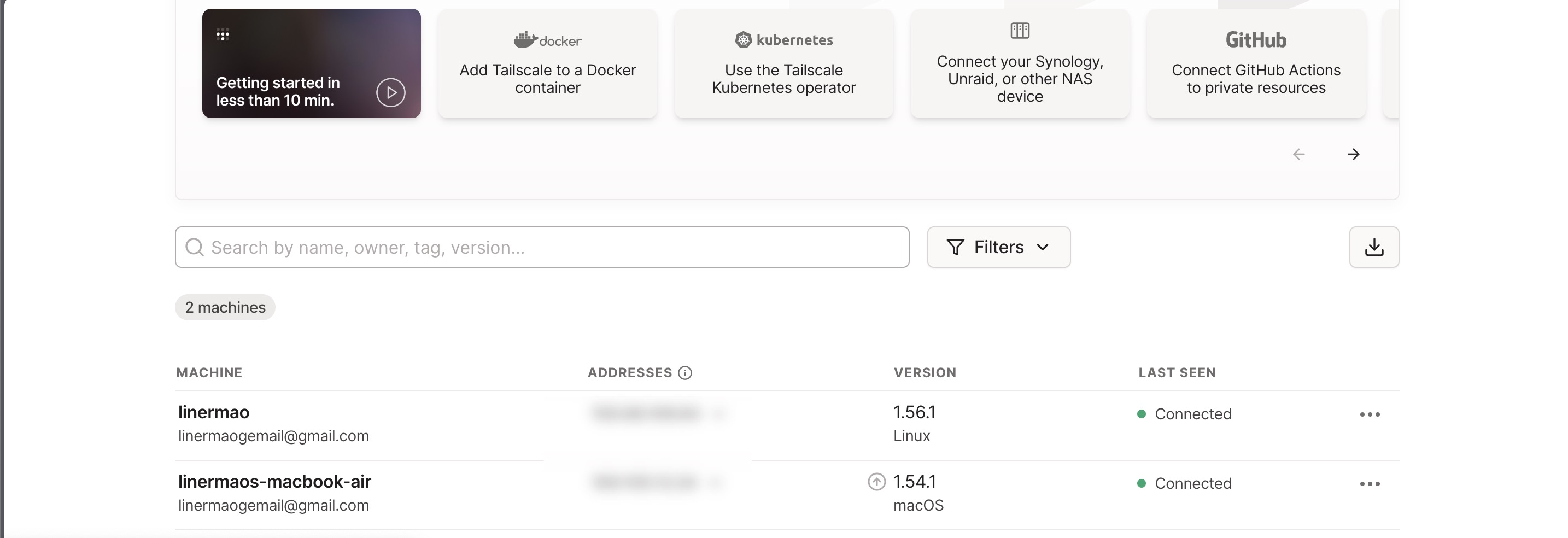
Figure-1
1.3 How to configure
Make sure your linux device have allowed SSH connections. Some systems don’t come with OpenSSH installed, so you need to run “apt install openssh-server” first. Then allow ssh use port 22 and allow password authentication.
What is openssh-server: OpenSSH is a freely available version of the Secure Shell (SSH) protocol family of tools for remotely controlling, or transferring files between, computers.
sudo vim /etc/ssh/sshd_config |
Now, you can use your main device to establish an SSH connection with your remote device for testing purposes:
ssh user_name@your_tailscale_ip_address |
1.4 Use ssh-keys instead of password
Using SSH keys with an SSH agent allows users to connect to a server or multiple servers without requiring the user to remember and re-enter their password when logging into multiple solutions, making for faster, easier and safer log-ins.
# create ssh-key |
Then you can permit password authentication for safety.
#PubkeyAuthentication yes |
1.5 Simplified linking commands
Always use long command can be a trouble for lazybones, you can easily use alais to do it.
# open shh config or create if no files |
